Enhancing SSH Users Management for Security
For security reasons, the ARM blocks remote root login into ARM VM Linux machines for both ARM Configurator and ARM Router. The feature prevents accidental damage of ARM system files available for the root user. External hackers typically attack the root user because the root account is the most vulnerable and can be attacked remotely via SSH. Instead of the root user, operators can use the armAdmin SSH user. During a first-time installation of the ARM or an upgrade to ARM 9.0 or later, this account is created with a default password and the root account is blocked for remote access.
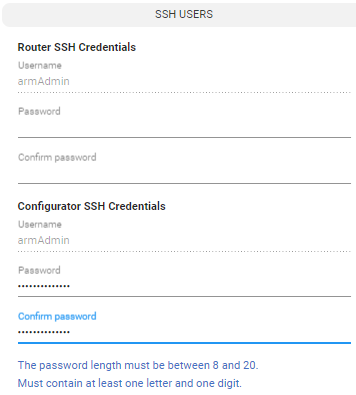
The operator can change the default password for an armAdmin SSH user. The same password should be shared by all ARM Routers and it can be different to the Configurator’s armAdmin password.
| ➢ | To configure enhanced SSH users management for security: |
| 1. | Open the Security page (Settings > Administration > Security) and locate section SSH Users. |
SSH Users
Starting from ARM 9.0, log in to ARM machines using the armAdmin user and request root access only when powerful root privileges are required. After a remote login using armAdmin, switch to root user by applying the “su-“ command. This switch of privileges is required for the following ARM maintenance operations:
| ● | ARM upgrade (starting from ARM V.9.0 and later). Note that upgrade to ARM 9.0 from the customer’s previous load still requires root privileges. |
| ● | ARM Backup and Restore |
| ● | Logs collection (logCollect) |
See the ARM Installation Manual for more information.